The research findings of this project were showcased at the 6th IEEE International Conference on Industrial Cyber-Physical Systems (ICPS) held in Wuhan, China in 2023 by our Cyber-Physical Systems Lead, Dr Andrei Petrovski and his PhD Student, Otokwala Uneneibotejit. The conference papers have been officially published on IEEE Xplore (accessible here) and explored a lightweight (in terms of computational resources used) approach that could make intrusion detection faster.
What is an Industrial Control System?
An Industrial Control System (ICS) is a network of connected equipment that work together to manage physical devices in industrial settings. Nowadays, such systems play a crucial role in modern industrial processes, facilitating automation, optimization, and efficiency enhancements across various industries. ICS come in different types, including Supervisory Control and Data Acquisition (SCADA), Distributed Control Systems (DCS), and Programmable Logic Controllers (PLCs). At the same time, these systems pose cybersecurity risks as they are more frequently linked to corporate networks and the internet, rendering them susceptible to cyber threats. Hence, ensuring the security and robustness of industrial control systems is highly imperative.
What Are Cyber-Attacks?
Cyber-attacks refer to any malicious effort to disrupt, harm, or access computer systems, networks, or digital devices without permission. When successful, these breaches can render systems unresponsive to legitimate requests. Various examples of cyber-attacks include Malware, Phishing, Denial-of-Service (DoS), Distributed Denial-of-Service (DDoS), Man-in-the-Middle (MitM), SQL Injection, Zero-Day Exploits, Insider Threats, and most importantly Advanced Persistence Threats (APTs).
Project Aim
With the advancement of technology, ICS have been integrated with corporate intranets and the internet, thereby exposing previously isolated systems to a variety of cyber-attacks. Particularly notable are the vulnerabilities in the Modbus protocol, still commonly used in ICS, which pose challenges for data obfuscation and secure communication among component entities. This project aims to implement a lightweight intrusion detection system using a Common Features Technique (CFT) approach from an ensemble feature selection strategy.
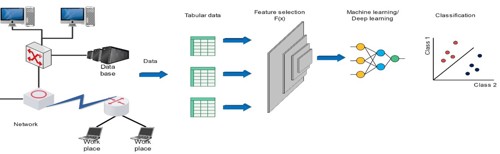
Project Overview
Feature selection methods like Information Gain, Chi-Squared, and Gini Index were explored to rank the features of the datasets based on their significance relative to the target class. By using an ensemble of these approaches, the goal was to ensure the selection of non-redundant features for further processing. This approach aimed to address the limitation of using a single feature selection method, which tend to select suboptimal features that work well only for certain algorithms. The CFT approach involves selecting varied features, which are then used in machine learning models such as Random Forest, Support Vector Machine), K-Nearest Neighbours and deep learning models for efficient data classification. In addition, the CFT data were further subjected to dimensionality reduction using the Long Short-Term Memory (LSTM) Autoencoder to enhance its computational efficiency and run-time. Through CFT and a reduced feature set, the method proved effective in detecting intrusions, showing comparable performance to existing models.
Ongoing Work
While the project has been optimized through LSTM Autoencoder, there is also a plan to expand the project further. The aim is to tailor the intrusion detection strategy to target specific vulnerabilities commonly found in the Modbus protocol. This extension is currently under consideration to enhance the project’s effectiveness.
To discover more about how our Cyber-Physical Systems team is solving real-world problems and the other impactful research projects that are currently being undertaken, view our dedicated Cyber-Physical Systems webpage.








